We shoulder responsibilities for sustainability
by incorporating ESG foundations in our DNA at Ennostar
Information security and privacy controls have become an essential part of business. Ennostar and all subsidiaries have formulated information security policies to protect client privacy as part of our responsibilities and to prevent unauthorized use of computer systems in accordance with the “Regulations for Protection and Management of Personal Information.” Users of all departments are required to apply for user codes and applications, and can only obtain formal access to computer systems following approval by unit supervisors and information technology office managers. Personnel not involved in operations are unable to obtain customer information.
Our parent company has established a dedicated information security management department responsible for information security maintenance, information security frameworks, information security policies, and other information security projects and review procedures to lead our subsidiaries in joint realization of Ennostar information security goals.
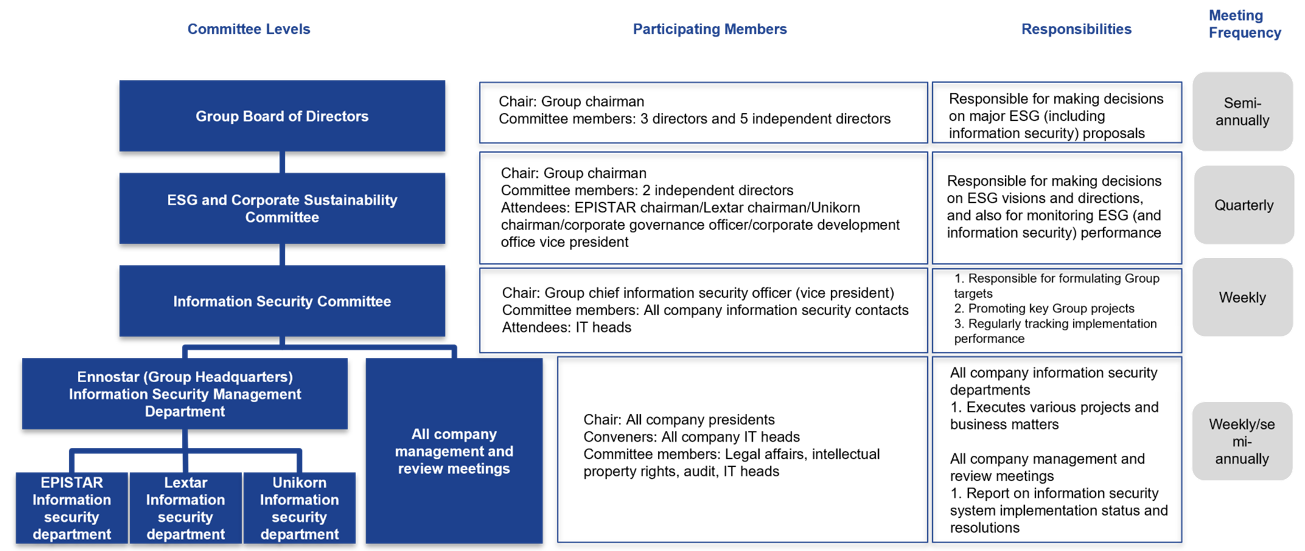
The Group established the “Information Security Committee” to facilitate review of information security implementation strategies, goals, and performance. The Board makes up the first level of our information security framework and is responsible for making decisions on major information security proposals. The Corporate Sustainability and Risk Management Committee (chaired by the Group chairman) makes up the second level of our information security framework and is responsible for determining the Group’s information security directions and goals. The Information Security Committee (chaired by the chief information security officer) makes up the third level of our information security framework and is responsible for promoting Group goals and key projects. The information security departments of each subsidiary make up the fourth level of our information security framework and are responsible for implementing various targets and projects. We convene information security management and review meetings twice every year, and report information security implementations and resolutions to the presidents of each subsidiary.
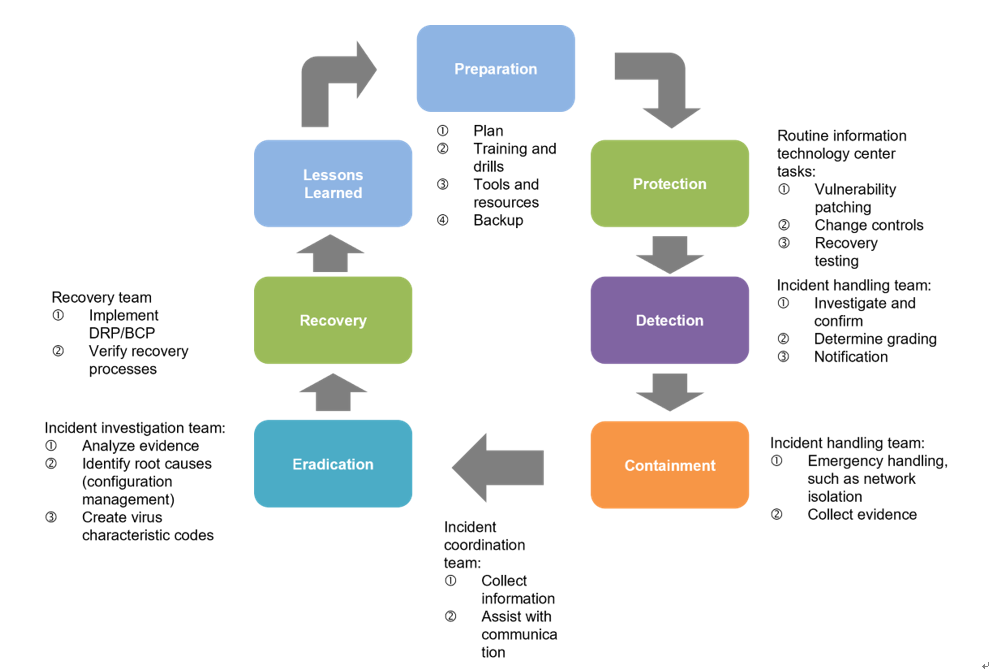
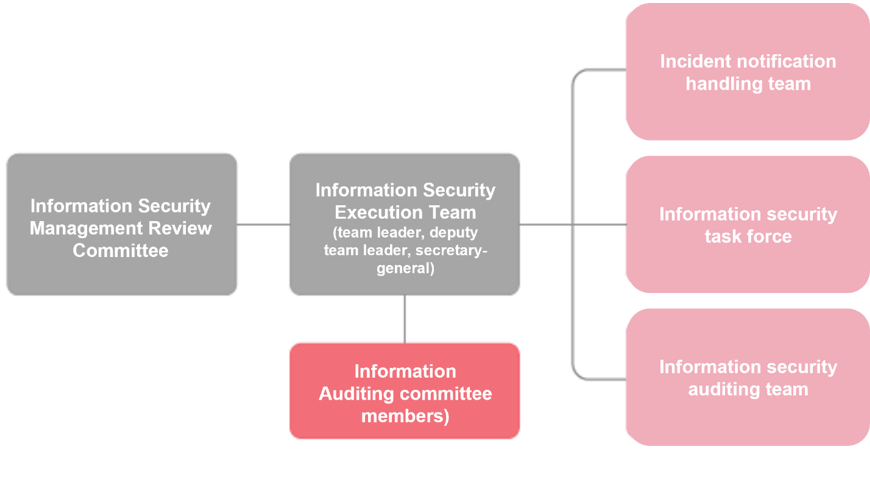
We have also established an “Information Security Execution Team” to disseminate information security concepts throughout the Group, and to implement regular drills and information classification systems for incident management. We conduct annual drills for ransomware scenarios to strengthen employee understanding of incident responses and to speed decision-making and notification procedures during incidents.
Information Security Organizational Structure
To ensure information security, achieve the quality expected by our customers, and protect customer privacy, the Group adhered to ISO 27001 requirements in formulating corporate information protection and management processes. In 2023, the Ennostar Group obtained ISO 27001 Information Security System verification for all factories in Taiwan and established information security procedures which comply with international standards. We hope that these international verifications can reduce corporate information security threats, establish the highest standards for protection of confidential information, and protect customer intellectual property rights, process parameters, and other confidential information.
To reduce possibilities and impacts of risk incidents, the Group actively implements management systems and risk response measures. We not only incorporate third-party information security risk assessments, but also conduct routine inventories of information assets, account checks, and internal audits each year, as well as convene information security management and review meetings attended by our president and managers from relevant units. Ennostar and all subsidiaries in Taiwan also conduct business continuity drills once every year. At present, all Group subsidiaries have received A ratings on third-party risk assessments, exceeding average industry ratings.